Operation Triangulation Ends The Apple Security Myth
With the recent discovery of Operation Triangulation by security researchers at Russian AV company Kaspersky Labs, the murky world of global espionage with corporate complicity is revealed in full colour. All the evidence points to Apple being a secret partner in enabling NSA spy operations. If your iPhone is XS or newer then you are vulnerable. Here’s how to fight back against Nation-State Spyware.
BTW: This vulnerability in Apple Silicon was reported here previously – M1 Critical Flaw Discovered – although we did not realise the international significance. Apple paid out through their Bug Bounty program to keep the story secret.
Kaspersky Labs FTW!
Gone is Apple’s claim to being fiercely protective of their customers & independent of government influence – they’ve repeatedly lied & been caught out before – this seems to be corporate policy so do not expect this to change. The obvious conclusion from reading the lengthy, intensive study published on SecureList by Kaspersky is that in 2019 Apple inserted a hardware component on all iDevice boards – most likely at the behest of American spy agency NSA – that has no purpose other than to provide a secret back door entry. That’s straight up shitty behaviour by any estimation & now they’ve been found out.
Since the release of iPhone XS in 2019, every single iDevice sold worldwide has had a vulnerability to a highly sophisticated zero-click iMessage attack that runs with elevated admin root privilege, allowing the attacker (NSA) to take control of the iDevice without any obvious indication. For the last 4+ years, USA spymasters have had unprecedented privacy-breaching access to virtually any iPhone/iPad/MacBook/iMac sold worldwide.
If you use an iPhone XS or newer, your privacy can be invisibly breached & massively invaded without you being aware!
FA&FO
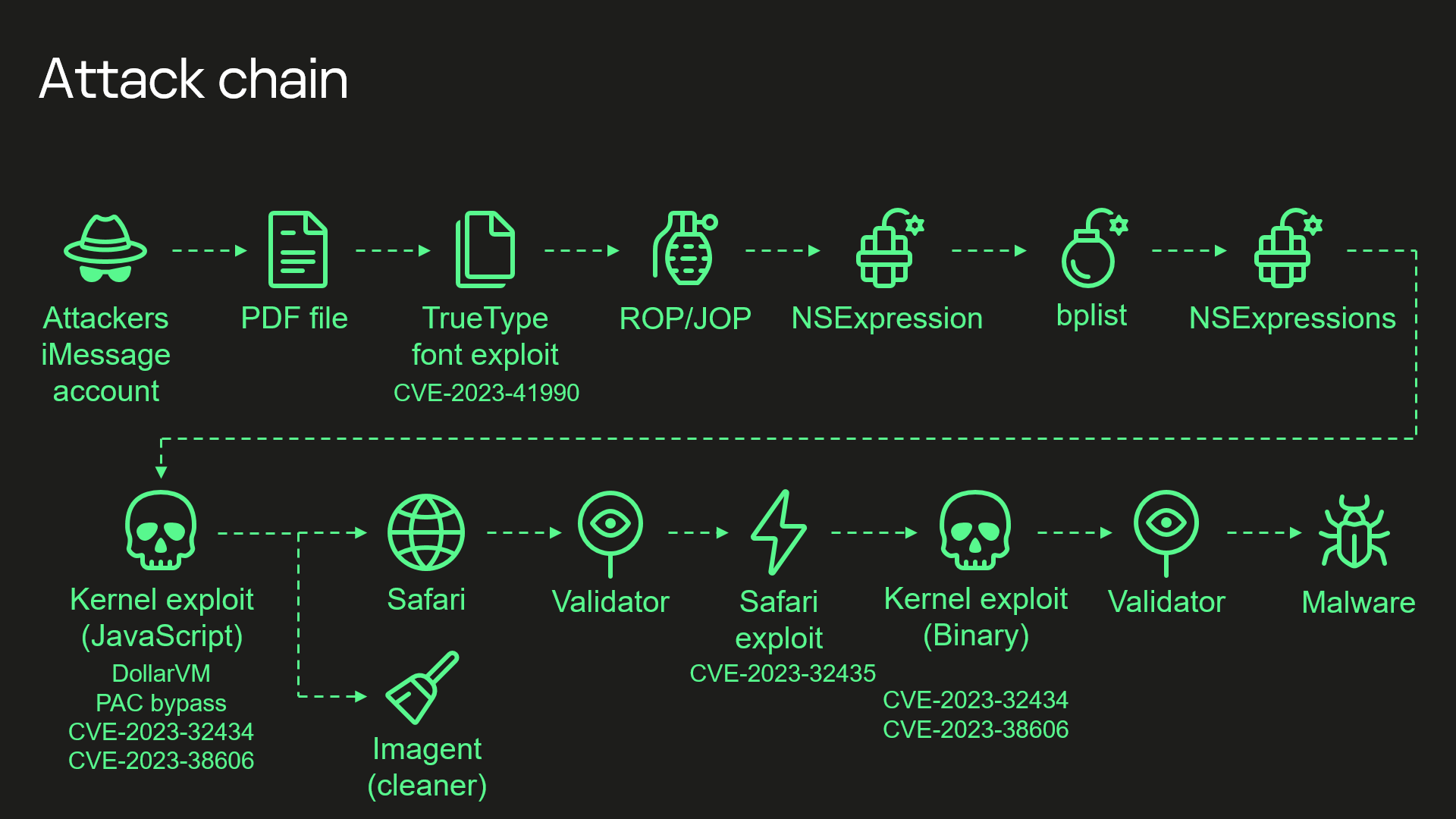
In a classic case of “fuck around & find out”, Operation Triangulation was discovered when the NSA chose to infect iPhones used by the security researchers at Kaspersky Labs – people whose profession it is to find, identify, reverse-engineer & resolve attacks on all manner of IT infrastructure. Their comprehensive study resulted in publication of the entire event chain, ending the NSA’s 4-year run of privacy-invading data harvesting from iPhones, iPads, MacBooks, iMacs & Mac Pros.Apple Security Myth Shattered
A major unintended side-effect of the fuck around & find out principle is that the reverse-engineered code creates a golden opportunity for a powerful new universal iCloud bypass to be built. Where the original exploit was a tightly-held secret between Apple & the NSA, the second iteration will be public-facing & used on far more late-model iPhones & iPads – all those delicious items you wanted but couldn’t justify the expenditure. The vulnerability exists in all Apple silicon devices, so shortly after an iPhone / iPad iCloud bypass is developed we can expect a solution to locked M1 & M2 MacBook, iMac, Mac Studio & Mac Pro hardware too – the Apple security myth is shattered. But in the meaning time, if you’re a “person of interest” to the NSA who uses an iPhone – activist, politician, public official, military officer, journalist, business owner, high-ranking company officer, reporter, publisher or just someone whose name happened to pop up – all the information gathered by your iPhone has been available to the NSA. A quick Google search for the technical indicators of an Operation Triangulation-compromised iDevice indicates that this could be far more than a specifically-targeted weapon – there are thousands of posts in IT forums from seemingly everyday average people enquiring why their iPhone is contacting unusual C2C sites in their DNS logs, amongst other indicators.Organisations of interest to nation-state surveillance typically have substantial resources to mitigate the effects of Operation Triangulation – think Greenpeace, Sea Shepherd, Hamas, United Nations QUANGO’s but what about those smaller targets, those without a dedicated IT security team, even individuals such as freelance journalists – what can they do to fight back against Operation Triangulation surveillance?
How To Identify Operation Triangulation
There is one easy way to tell if your iDevice has been targeted by Operation Triangulation – no successful iOS updates. The highly-sophisticated spyware protects itself from being overwritten or patched out by blocking iOS updates. Users will still see that there is an update available but installation will fail with “Software Update Failed. An error occurred downloading iOS.” Because iOS updates do sometimes glitch out, & their iPhone still works on non-updated firmware, the targeted user won’t necessarily see this as a sign of incredible danger.
Go Settings, search Update to view which iOS your iPhone is running. If it’s lower than iOS 17.2 (which seems to patch the Operation Triangulation vulnerability) then you should have an update available. Try to install – if you can’t then you urgently need a new phone – & a forensic examination & re-evaluation of your business & personal activities.
The best basic advice I can give anyone using smartphones to communicate is to use Signal Private Messenger.
That you cannot update is NOT an absolute definite indicator of Operation Triangulation infection – although if you are compromised, you will not be able to update. The good guys @ Kaspersky (who else?) have created a free tool for absolute confirmation of infection. Cleverly named Triangle_check, the utility examines a local back up of your iDevice so you’ll need a computer for this operation. Triangle_check is available as a Python script for MacOS or binary build for Windows & Linux.
Mitigation & Defence
If you can’t get a new phone today then grab a Windows PC, install 3U Tools & follow their instructions to put your phone in DFU mode before updating to the latest iOS using 3U’s non-recoverable user data flash method. Updating will remove all traces of Operation Triangulation along with every other piece of your personal User data – the iPhone that you & the NSA have been sharing will return to factory-fresh setup mode after updating.
I don’t recommend restoring from iCloud or local backup – for obvious reasons. Sorry about the inconvenience, it’s well worth it though.
Operation Triangulation spyware has not yet been found on iDevices running iOS 17.2 or later, so this update will *most probably* keep you safe. Shut down the entry point for the attack by disabling iMessage (use Signal instead). Further surety is provided by enabling Lockdown mode & rebooting regularly.
Be Aware, Stay Alert
Operation Triangulation was obviously a major long-term success for USA’s boss spy agency NSA. Apple’s proprietary iDevice family gave them a single platform to attack. Apple’s integrated family – cross-platform hardware delivering iMessage functionality to all products was an unbelievable opportunity for the NSA to create a universal malware – the information gathered must have come in like a data firehose, they would have required substantial infrastructure just to capture & process the
Android devices don’t offer such a target. Even the dominant Samsung Android phones are sold with a variety of chipsets – Exynos, Qualcomm, MTK or SPD. Often a single model will be available with Exynos CPU in some markets & Qualcomm in others. Consumers see it as one phone, but under the surface it’s an entirely different device. Use the model number to identify the variant – SM-S901B is an Exynos 2200-powered Galaxy S22 while SM-S901E has a Qualcomm SM8450 chipset. This strategy denies the opportunity for such a universal attack platform.
Qualcomm, however, are an American company, as are Google. South Korea is an American ally. The possibility definitely exists that Samsung & Qualcomm have been subjected to the same requirement as Apple were, maybe in conjunction with Android OS owner Google. Just because it hasn’t been found, don’t think that there isn’t a similar NSA program for spying on Android handsets.
I very much doubt that the Chinese manufacturers would accept NSA demands for a secret hardware component to be installed. Huawei & Oppo in particular make industry-leading products, as do Xiaomi.
Huawei’s P60 Pro & Mate 50 Pro are among the very best handsets available today, Oppo’s Find X5 Pro is awesome hardware & their N-series foldables don’t suffer the repeated screen failures that Samsung’s Z range is infamous for.
Both manufacturers have had their hardware repeatedly examined in microscopic detail. Suspicious spyware components have yet to be found. I’d be leaning towards purchasing top-end Oppo or Huawei product as a pre-emptive defence against being exposed to an Android version of Operation Triangulation.
Hypocrisy Much?
How ironic that both Trump & Biden administrations have legislated against major Chinese brand Huawei because of possible – but unproven, even today – spyware installations yet at the very same time American poster-child company Apple was installing the Operation Triangulation hardware at the behest of the boss spy agency of the US government. Hypocrisy much? But what would you really expect from a nation that believes that cheese comes from an aerosol can?
OMFG! I’ve been trying to update my iPhone 13 Pro for 18 months without success. Now I know why – & I’m not in the slightest bit interesting to a spy agency. Well, maybe…